South Korean web hosting company Nayana agreed to pay $1 million in Bitcoin after a ransomware attack hit 153 Linux servers.
The attack took place June 10 and resulted in over 3,400 business websites the company hosts being encrypted. According to the Nayana’s initial announcement, the attacker demanded 550 Bitcoins (over $1.6 million) to decrypt the infected files. Following negotiations, they lowered the ransom demand to 397.6 Bitcoins (around $1.01 million).
The payments, the company announced, will be made in three batches, and the attackers will decrypt the affected servers accordingly. Two payments were already made, and the company is currently in the process of recovering the data from the first two server batches.
The ransomware used in this attack, Trend Micro reveals, was Erebus, a piece of malware that was initially spotted in September 2016 and which was already seen in attacks earlier this year, when it packed Windows User Account Control bypass capabilities.
Apparently, someone ported the ransomware to Linux and is using it to target vulnerable servers. Running on Linux kernel 2.6.24.2, which was compiled back in 2008, Nayana’s website is vulnerable to a great deal of exploits that could provide attackers with root access to the server, such as DIRTY COW, Trend Micro notes.
This version — analysis here by AhnLab, Hauri, and Trend Micro — targets only Linux computers. It is unclear if the two Windows versions spotted previously are related to the Linux version that hit Nayana, or if this is just another case where crooks used the same name for their ransomware strain.
Once the encryption process ends, it drops two ransom notes named "_DECRYPT_FILE.html" and "_DECRYPT_FILE.txt" on the user's desktop. Payments are handled via two Tor onion sites,
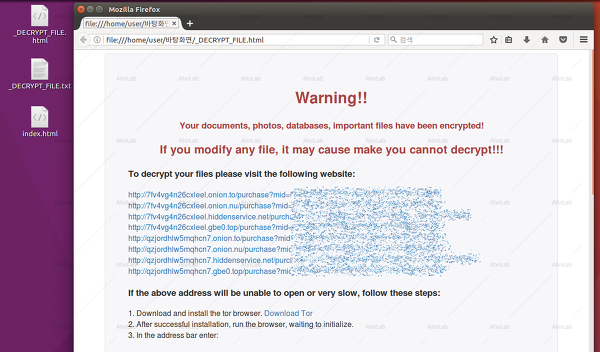
Erebus Linux ransomware - ransom note [Source: AhnLab]
A Trend Micro analysis of the Nayana systems reveals serious problems with both versions and configuration. No wonder that they fell victim to this infection. Did they have a false sense of security that Linux is ransomware-proof?
NAYANA’s website runs on Linux kernel 2.6.24.2, which was compiled back in 2008. [...] Additionally, NAYANA’s website uses Apache version 1.3.36 and PHP version 5.1.4, both of which were released back in 2006. Apache vulnerabilities and PHP exploits are well-known;[...]. The version of Apache NAYANA used is run as a user of nobody(uid=99), which indicates that a local exploit may have also been used in the attack.
 What is really the best way to combat the threat of ransomware?
What is really the best way to combat the threat of ransomware?
We surveyed businesses across all industries to find out what they're doing to defend themselves. We thoroughly examined who is at risk, what the scope and cost of an attack is, how organizations are protecting themselves from ransomware, and the effectiveness of their endpoint protection. The results might surprise you!
Learn more about:
- The impact of an attack
- How effective is antivirus against ransomware?
- What are the best prevention methods?
- How to strengthen your last line of defense - your users
Don't like to click on redirected buttons? Here is the direct link:
https://info.knowbe4.com/endpoint-protection-ransomware-effectiveness?
@Credits: KnowBe4



























