5 most important vulnerabilities every developer should be aware of

It takes 20 years to build a reputation and few minutes of cyber-incident to ruin it. — Stephane Nappo
Who am I?
I‘m a full stack develeloper from Germany with many years of experiences in web development and web security. I first started programming with PHP — and yes, those applications were crap relating web security! This article deals with 5 of the most common vulnerabilities elaborated by OWASP.
1. Injection
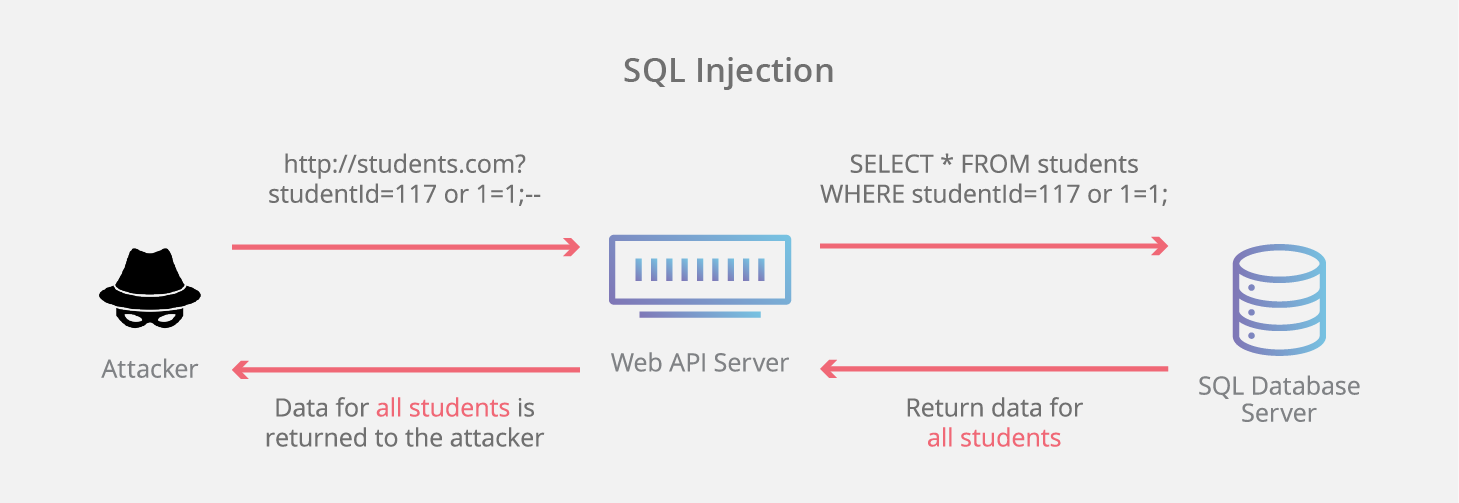
Since Web 2.0 users are able to create their own posts and submit data to a database. If a website, app, or device incorporates user input within a command, an attacker can insert a “payload” command directly into said input. If that input is not verified, an attacker then injects and runs their own commands.
Prevention
If you use frameworks, make sure to always keep them up to date! If you don’t use frameworks, make sure to use prepared SQL Statements! This will close the vulnerability, because the attacker can’t break out of the statement anymore.
2. Broken Authentication

When you offer user authentication on your website, the server identifies the user with an unique Session ID or JWT. If the attacker steals the Session ID (Session Hijacking) of your victim, he can send requests to your server with that unique Session ID. Your server would think, the request is coming by your victim.
Prevention
- Session IDs should timeout: User sessions or authentication tokens should be properly invalidated during logout.
- Do not send credentials over unencrypted connections: Passwords, session IDs, and other credentials should not be sent over unencrypted connections.
- Maybe add some more identification rules to the server. For example restrict the Session ID to be only used by the IP, which generated the Session ID.
3. XSS (Cross-Side-Scripting)

XSS allows mailicous code to be added to a webpage, for example by a user comment. When a user adds a comment to a webpage, the site will save this comment to the database. When other users want to see the comment, the webpage writes out the code in an HTML document. The problem with that is, that a mailicous user could enter content that includes HTML entities like the <script> Tag.
Prevention
XSS is very simple to prevent. The easiest way is to escape user input. Escaping data means taking the data an application has received and ensuring it’s secure before rendering it for the end user.
Or you could validate the user input:
The theory goes like this: Expect any untrusted data to be malicious. What’s untrusted data? Anything that originates from outside the system and you don’t have absolute control over so that includes form data, query strings, cookies, other request headers, data from other systems (i.e. from web services) and basically anything that you can’t be 100% confident doesn’t contain evil things.” — Troy Hunt
4. Using Web components with known vulnerabilities
Nowadays as a developer you don’t develop just with writing code. There are so many packages and dependencys you can/have to include into your project, doing so much work for you — thanks to open source!
However: The more packages/dependencies you include in your project, the more doors your potentially open!
Prevention
Keep your packages up to date! Often when a development project is finished and running in production developers get new projects and the old projects runs, runs and runs. But by the time, dependency vulnerabilities get fixed. But if you don’t update them in your project, those vulnerabilities stay open for the attacker.
There are great tools for automating finding & fixing vulnerabilities in your dependencies. You should definitly check out Snyk.io!
5. Sensitive Data Exposue
First: Always encrypt sensitive data. Always. You don’t want to store credit card numbers, health data or passwords in plain text! If data is stored or transfered as plain text, if older/weaker encryption (please dont use md5 anymore) is used, or if data is decrypted carelessly, attackers can gain acces and exploit the data.
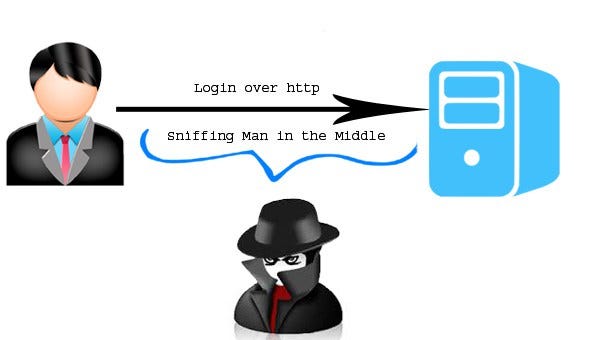
Prevention
- Encrypt sensitive data and define accessibility
- Use SSL/TSL !
Final Words
Over the time, web security has become increasingly important. Nowadays we transfer our most sensitive data like health or financial data through the internet. If you want to keep your systems safe against attacks, regulary check your applications for vulnerabilitys. You should definitly have a look at OWASP, offering the most important vulnerabilities.
Coming soon: For this article I developed a crappy web application (regarding web security) vulnerable for attacks like XSS or SQL Injection. I am going to make a public github repository including the source code and explanations for how to attack the site and how to fix those vulnerabilities.

@Credits: Medium



























